European Cybersecurity Legislation
For many years now, Europe has been leading the legislative landscape at the cybersecurity level, being an example and source of inspiration in this area for the rest of the countries outside the Union.
Starting with the GDPR, published in 2016, focused on data privacy for both individuals and legal entities. This same year also saw the release of eIDAS, establishing guidelines for electronic identification and transactions.
In 2017, the NIS Directive was made public, proposing measures aimed at ensuring a high common level of security of the European Union networks and information systems. The commission is currently working on an NIS 2 Directive that will expand the sectors of application and force all medium and large companies in each sector to have to comply with the directive.
In January 2020 the 5G Toolbox was published, the objectives of this toolbox are to identify a possible common set of measures capable of mitigating the main cybersecurity risks of 5G networks.
At the end of the same year, the new European cybersecurity strategy was published, which included cybersecurity certification among its priorities.
What does the Cybersecurity Act consist of?
During 2019, the foundations were laid for what would become the new European Cybersecurity Act regulation, which proposes the creation of a common European framework for the certification of "cybersecure" ICT products and services. This initiative was possibly the most daring to date because of its innovative approach.
One of the main objectives of the Cybersecurity Act is to increase the competitiveness and growth of European companies, to move from being cybersecurity importers to cybersecurity exporters.
Key to this is the ability to issue cybersecurity certificates recognized throughout Europe for systems, processes and products while minimizing their cost.
The Cybersecurity Act aims to achieve this objective by creating a common European framework for the development of common schemes for cybersecurity certification.
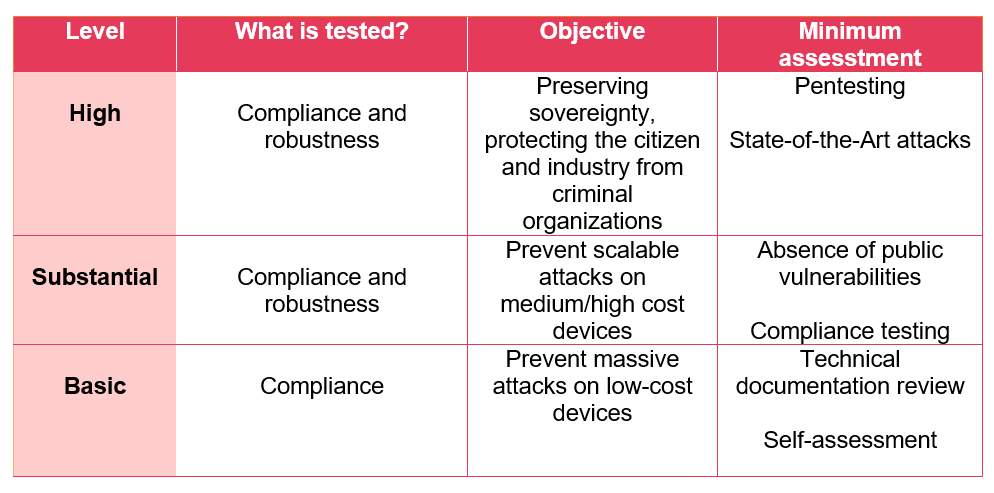
The Cybersecurity Act or CSA sets out three levels of assurance (basic, substantial and high) that will allow the evaluation of systems, processes and products based on the following summary table:
Main actors in the process of creating the new European certification schemes
There are several players that enter the scene once the Cybersecurity Act is passed. The first of these is ENISA (European Union Agency for Network and Information Security) which assumes the role of the new European Agency for Cybersecurity, and whose task is to coordinate and harmonize policies concerning cybersecurity at European level, supporting Member States in the implementation of plans and strategies.
One of the first steps taken by ENISA in 2019 was to create the SCCG (Stakeholder Cybersecurity Certification Group), a select group of stakeholders including jtsec whose role is to offer advice on strategic issues related to cybersecurity certification and assist the European Commission in the preparation of the URWP (Union Rolling Work Programme), an annual document that describes the priorities in the creation of new cybersecurity certification schemes.
CCN (Spanish National Cryptographic Center) , for its part, as a Spanish national cybersecurity certification authority (NCCA), represents Spain within the ECCG (European Cybersecurity Certification Group). This group assists the European Commission in the implementation of the European certification framework.
In addition, for each candidate scheme, ENISA builds an ad-hoc working group with industry experts to support ENISA in the preparation of the scheme.
URWP, an essential logbook.
The need for the several certifications and initiatives to be successful has led the European Commission to draw up a roadmap to be followed, the so-called URWP.
This document created by the European Commission defines the priorities at European level in terms of cybersecurity certification. It is, therefore, a document to be taken into account by manufacturers, Public Bodies and companies related to the cybersecurity certification sector. .
The URWP contains a series of strategic lines of action, five to be precise, which focus on improving cybersecurity in the European Union as a whole, covering both the public and private sectors:
The proposal set out by the European Commission and embodied in the URWP is ambitious, with Europe adopting a leadership position in terms of cybersecurity certification whose schemes serve as a basis at the international level.
Phases to be completed for the approval of a certification scheme in Europe.
The process for the acceptance of a scheme under the Cybersecurity Act is complex and has different phases, which is why consensus within the community is important.
There are four main phases:
1. Creation of the URWP (Union Rolling Work Programme), which reflects the European Commission potential cybersecurity certification schemes and is reflected in the aforementioned document.
2. For each potential new certification scheme, the European Commission requests ENISA to create it. ENISA, together with the SCCG and the ad-hoc working groups prepare a candidate scheme.
3. A public consultation of the candidate scheme is made and sent to the European Commission.
4. After approval by the European Commission, the candidate scheme becomes law.
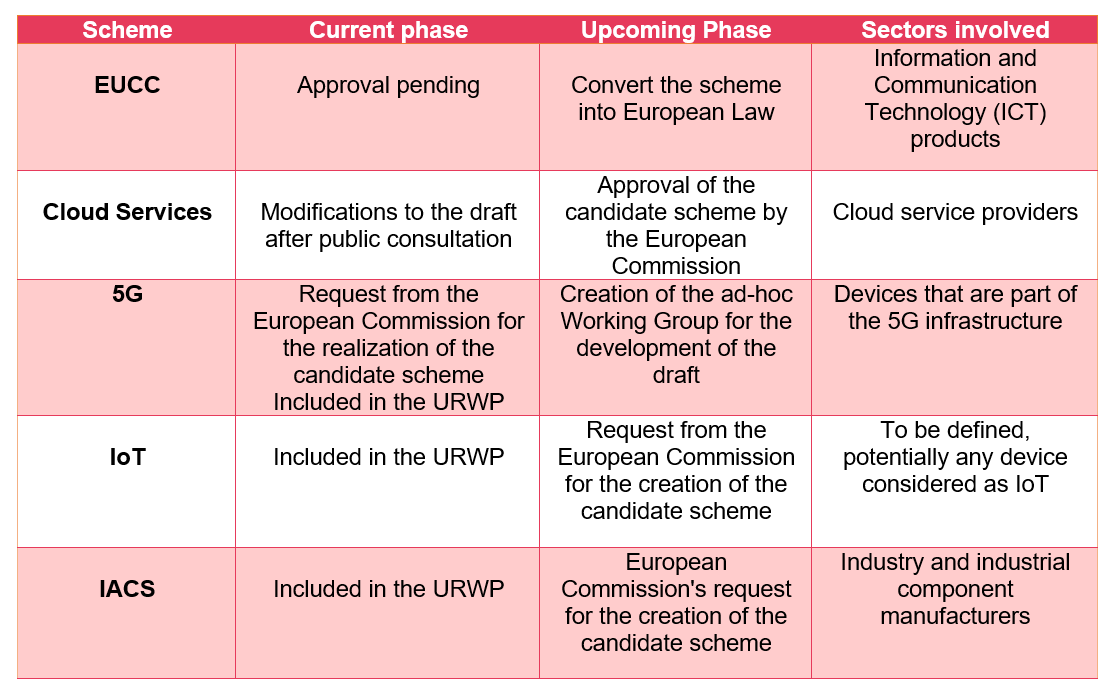
European cybersecurity schemes under development, EUCC and Cloud Services.
There are currently two schemes on the table that will be approved by the European Commission in the coming months. The most advanced and expected to be approved in the second quarter of this year is the EUCC or Common Criteria based European Candidate Cybersecurity Certification Scheme, developed for the cybersecurity certification of ICT products and whose essence lies in the international Common Criteria standard and the European recognition agreement SOG-IS On this basis, already known to all, substantial improvements have been made, such as patch management or greater agility when updating the version of an updated product.
A transition period is expected for the application of the EUCC, necessary for the adaptation of manufacturers, laboratories and Certification Bodies, taking into account that there will be no parallel issuance of the new EUCC certificates and the traditional Common Criteria.
The other certification scheme under development, but at a less advanced stage than EUCC, is the Cloud Services scheme. The candidate scheme completed the public consultation on February 7, so it is in the phase of making modifications if necessary. It is expected to be approved by the European Commission by the end of this year if the process is not seriously disrupted.
Future European cybersecurity schemes foreseen in the URWP.
The European Commission has mandated ENISA to develop a Scheme relating to 5G due to the importance and number of critical services that will depend on this technology. This mandate supports the objectives of the 5G Toolbox developed by the commission. ENISA is already setting up the ad-hoc working group that will initiate the preparation of the scheme and potentially reuse some of the work developed by GSMA in recent years.
URWP identifies two other schemes as priorities:
Looking to the future, the Commission envisages the creation of certification schemes for artificial intelligence, cryptography or secure development lifecycles.
The Commission is also considering the unification of the different lightweight methodologies created in Europe into a single scheme using the FITCEM (Fixed Time Common Evaluation Methodology) evaluation methodology.
The time is now
The Cybersecurity Act launched a number of obligations as we have already seen, but also a number of benefits. The main one is greater public confidence in the market and digital solutions, which will lead to greater demand for these solutions. In addition, for manufacturers and suppliers it is a moment of opportunity, improving competitiveness with respect to companies outside Europe.
After two years, we can affirm that now is the time to respond to the different challenges that the Cybersecurity Act faces us, both for the public and private sectors.
Manufacturers and suppliers must "move up a gear" to adapt and be prepared to certify their products.
Public Administrations, must provide sufficient resources to all the actors involved imminently, otherwise, there is the threat of not having the capacity to respond to the growing market demand..
Authors: José Ruiz y Javier Tallón.












