NIAP (National Information Assurance Partnership) is the body responsible for the implementation of Common Criteria in the United States, including the management of the Common Criteria Evaluation and Validation Scheme (CCEVS).
In the absence of a specific Protection Profile (PP) for Endpoint solutions, NIAP has recently developed two modules of the software application Protection Profile with the intention of facilitating the certification process for laboratories, consultants and developers themselves."
These two modules must be evaluated using the Software Application PP, published in March 2019, which imposes requirements on software applications running on any type of platform.
What is an Endpoint?
An Endpoint is a software that collects host data from endpoints to detect potentially unauthorized activity on the endpoints and allows threat hunting and other incident response actions to remedy malicious behavior. The platform on which it runs can be a physical or virtual operating system (OS), and on-premise or in a cloud environment.
This SW requires basic security features to block advanced malware that could infiltrate, prevent loss of valuable data, and provide secure access to email and applications.
This type of solutions are typically implemented in a client-server architecture where the Host Agent (client) connects to the server (EDR). This combination allows for greater scalability and increased protection of client devices
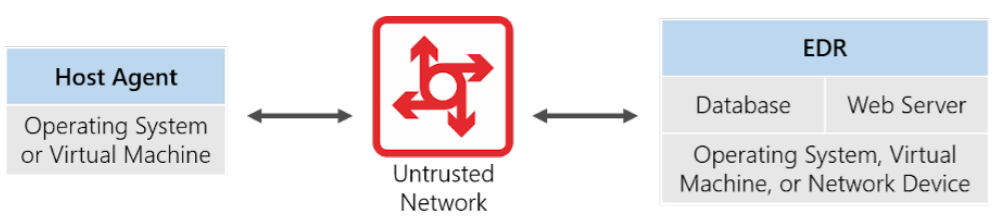
What are the modules based on?
The evaluation of an EDR system will require evaluations of different system components consisting of EDR and Host Agent. Each evaluation must meet the requirements on both the EDR and the Host Agent in addition to its base application software.
The development of these modules improves and contributes to the continuous development of the Common Criteria methodology, as well as to the improvement of cyber security for Endpoint type solutions.
jtsec’s recomendations for a Common Criteria evaluation.
As Common Critera experts consultants and evaluators, we always recommend to check first if the product we want to certify can fit a PP, which simplifies the process.
It is always recommended to get the help of a cybersecurity consultant before starting the process, as it is not easy to certify a product under the Common Criteria standard and a lot of time and money can be lost if the basis of the certification is not the right one. Therefore, the correct creation of a Security Target is the foundation for the rest of the certification process to be as smooth as possible.
At jtsec we are currently carrying on a Common Criteria evaluation with an Endpoint technology that we estimate will be completed during the Q1 of 2021.












