Cybersecurity is an area that is continually advancing at a rapid pace. Therefore, certifications must be modified to conform as closely as possible to reality and current events.
At jtsec we believe that collaborating in different working groups with different companies at a global level is the ideal way to contribute to the improvement and updating of the different cybersecurity certifications, mainly those that are more standardized worldwide.
A real example, the creation of a patch management extension for ISO/IEC 15408 and ISO/IEC 18045
Common Criteria (ISO/IEC 15408), is the most recognized and used cybersecurity standard internationally, accepted in more than 30 countries. At jtsec we are both consultants and evaluators (lab) for this methodology.
In this project we have the collaboration of Sebastian Fritsch, Head of CC Laboratory at the German cybersecurity consultancy and laboratory Secuvera for the creation of an extension for patch management for ISO/IEC 15408 and ISO/IEC 18045.
In this specific case, there is the problem that these standards do not allow re-certification of updates or products with security patches. Neither ISO/IEC 15408 nor ISO/IEC 18045 (or EMC) contain dedicated methods or assessment activities that support the evaluation of minor changes or minor updates. One of the most important aspects in the context of patch management and security updates is the characterization of changes in minor and major updates.
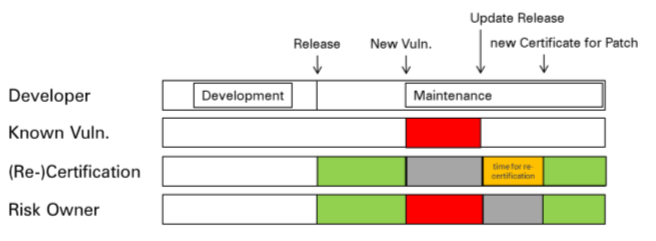
Thanks to the intense work of our Technical Manager, Javier Tallón and Sebastian, a serious problem was detected, which consisted of the fact that, after a new vulnerability was detected in a product, there was a time frame (until a new evaluation process was completed), in which the user had to choose between using a certified product or a safe product.
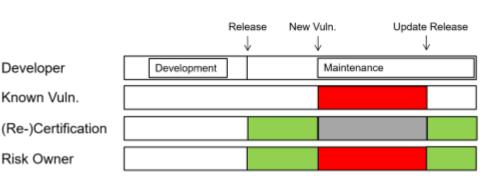
The solution offered is based on three pillars:
Other working groups of which jtsec is a member
We are involved in different working groups, we strong believe that the certifications should be increasingly accessible to all types of companies and that they should be valid in as many countries as possible.
All our efforts are aimed at building a more cyber-secure world and sharing our experience is the way to achieve it.












