Introduction
This standard provides the cybersecurity requirements for the Industrial Automation and Control Systems (IACS) as embedded components, network components, host components and applications. This standard aims to specify the security capabilities that must have a component to be integrated into a system environment with a given Security Level (SL).
Purpose
This standard is useful for system integrators, product suppliers, and compliance authorities (governments agencies and legal authorities) to perform audits to verify compliance with governing laws and regulations.
This standard will help system integrators to specify the appropriate security capability level of components that they need to use or acquire.
On the other side, this standard will help the product suppliers to understand the requirements to be supplied by the IACS components depending on the desired Security Level (SL). It is important to consider that sometimes an IACS component will not be able to meet the requirements required by a specific SL, however, it is possible to integrate it with a higher-level entity that meets the required SL.
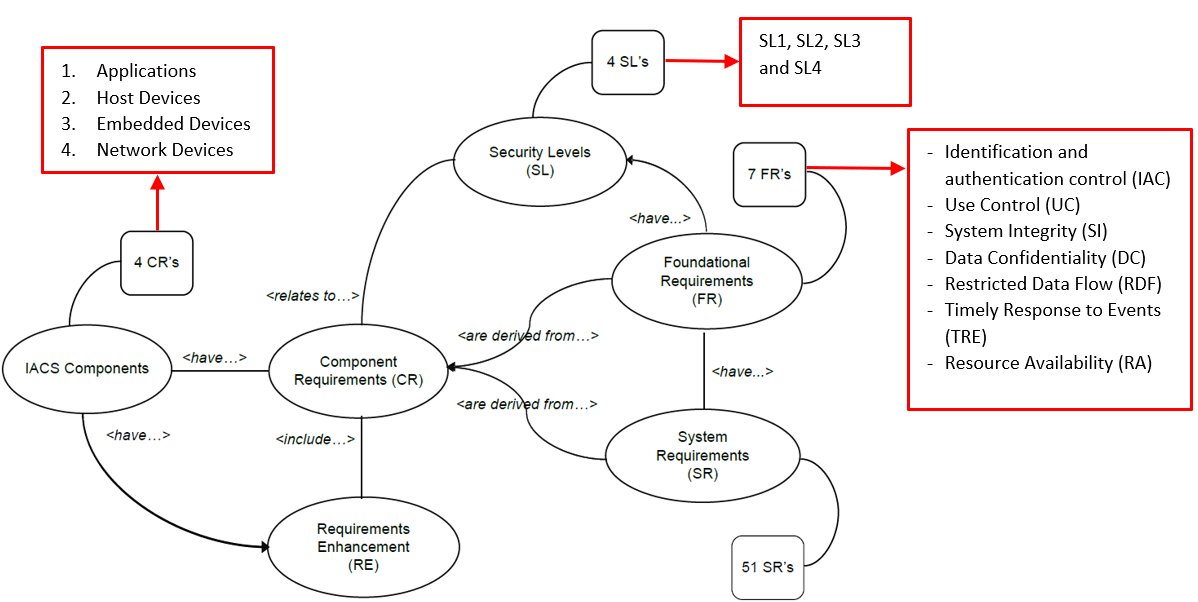
The requirements of this standard are defined for the following list of components:
- Application component requirements (ACR)
- Embedded component requirements (ECR)
- Host component requirements (HCR)
- Network component requirement (NCR)
Scope
The IEC 62443 standard (specifically the IEC 62443-1-1) defines a total of 7 Foundational Requirements (FRs) to comply with:
- a) Identification and authentication control (IAC)
The aim of this foundational requirement is to identify and authenticate human, software processes and devices to allow them to access to a system or assets to protect the application or devices requesting access to it before activating the communication. - b) Use Control (UC)
The main objective of this foundational requirements is to enforce the assignment of privileges once the user is identified and authenticated to allow him to do an action or set of them. The privileges will be assigned by the owner or system integrators. - c) System Integrity (SI)
The purpose of this foundational requirement is to ensure the integrity of the application or device to prevent unauthorized manipulation considering that: - The physical integrity must be maintained in both operational and non-operational states (such as during production, storage, maintenance, etc).
- The logical integrity must be protected while in transit and at rest.
- d) Data Confidentiality (DC)
This requirement aims to ensure the confidentiality of information to prevent unauthorized disclosure. This requires to protect communication channels and data stores against eavesdropping and unauthorized access. - e) Restricted Data Flow (RDF)
This fundamental requirement aims to segment the control system via zones and conduits to establish information flow restrictions and to determine the configuration of the conduits used to deliver the information based on a risk assessment methodology. The control should include mechanisms such as unidirectional gateways, stateful firewalls and DMZs to manage the flow of information. - f) Timely Response to Events (TRE)
The purpose of this key requirement is to respond to security violations by notifying the proper authority, reporting needed evidence of a violation and taking timely corrective action when incidents are discovered. Security policies and procedures and control must be established to respond to security violations using their risk assessment methodology using a risk assessment methodology. - g) Resource Availability (RA)
The aim of this main requirement is to ensure that an application or device is resilient against various type of DoS events (This include partial or total unavailability of application or device functionality).
Security levels
All the seven FRs detailed in the section above have 4 Security Levels (SLs). A higher Security Level requires a higher level of security measures and system requirements to comply with the specified FR. In addition, various Component Requirement are derived from the FRs and System Requirements.
| Security Level | Attack Type |
| SL-1 | Protection against casual or coincidental violation |
| SL-2 | Protection against intentional violation using simple means with low resources, generic skills and low motivation. |
| SL-3 | Protection against intentional violation using sophisticated means with moderate resources, IACS-specific skills, and moderate motivation |
| SL-4 | Protection against intentional violation using sophisticated means with extended resources, IACS-specific skills, and high motivation. |
The following table uses a colour code to summarizes the attack resistance depending on the Security Level and its attributes:
Conclusion
This standard makes possible to know what are the required security features to be implemented by the manufacturers in their IACs systems considering the security level to be met. This means that for each foundational requirement the manufactures shall implement the basic security measures to prevents attacks with low complexity or advanced security measures to prevent sophisticate attacks depending on the security level against the product is going to be evaluated.
Therefore, and high level will imply a higher effort on the manufacturer side but also a higher security strength that will require more knowledge and sophisticate tools from the evaluator and attacker side to try to avoid the implemented security means.
At jtsec we provide our E-Health and Industrial-IoT, services to develop your device complying with the requirements of the standard defined for each Security Level or to assess if your implementation already meets the requirements.












